I stumpled on a problem that the Azure backups were not going thru correctly and this was because the Azure Recovery services could not get proper contact with the Azure agent on the virtual machine. The Virtual machine in this case is a Oracle Linux deployed from the Azure gallery.
Investigate
SSH to the machine and make sure you got an account with sudo permissions.
First of, checked if the waagent was running
sudo systemctl status waagent
In my case, it was not running. Next step was to consult the logs that is located in /var/log/waagent.log. For now, this was empty and the old logs were compress .gz files. To unpack the compressed files
gunzip waagent.log-20180201.gz
After some searching around. The general tip was to update to latest version. To check current version, waagent has a switch for it. I also include the yum version that is the on the offical MS documentation sie
waagent -version
sudo yum list WALinuxAgent
My version was a low 2.0 version. So to check for updates, issue another yum command.
sudo yum check-update waagent
This will tell you if there is updates to your package.
Updating
To run the update, you issue yet another yum command
sudo yum install WALinuxAgent
This will update your waagent to latest version. This does not require a reboot.
Verifying
After we are done, we need to verify that the agent is running
sudo systemctl status waagent
In my case, it was running, but I got the following message
Warning: waagent.service changed on disk. Run 'systemctl daemon-reload' to reload units.
To quote a excellent stackexchange answer,
taking changed configurations from filesystem and regenerating dependency trees
What does “systemctl daemon-reload” do?
So proceeding, we need to wrap up and issue the daemon reload command to reload defination files.
sudo systemctl daemon-reload
Running the
sudo systemctl status waagent
will now not generate any errors – and the backups are running yet again.



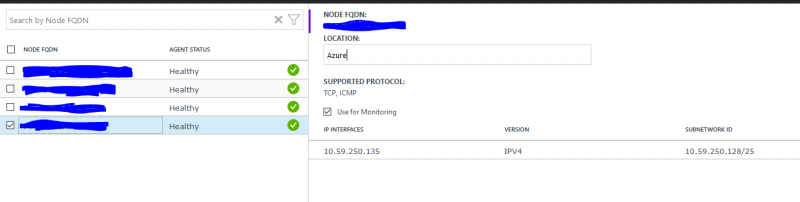 Note: If the OMS agent are not able to traverse with TCP 8084, only ICMP will been seen under Supported Protocol.
Note: If the OMS agent are not able to traverse with TCP 8084, only ICMP will been seen under Supported Protocol.